Quick Start
Currently, only Docker Compose based deployment is supported.
Using Docker Compose
To start Artemis, clone the https://github.com/CERT-Polska/Artemis/ repository and execute the
following 2 commands in your terminal in the Artemis directory:
cp env.example .env # you may also configure the settings (e.g. by providing a User-Agent to override the default one)
docker compose up --build
After that you should be able to access the Artemis dashboard at localhost:5000.
Note
Artemis exposes port 5000 that can be used to add tasks and view results. Remember that this port shouldn’t be available publicly, but e.g. on an internal network.
To add authorization (or SSL termination), you may for example use a reverse proxy, e.g. nginx.
We recommend you to add additional Artemis modules from https://github.com/CERT-Polska/Artemis-modules-extra/ - these modules haven’t been included in core due to licensing reasons, but provide additional features such as e.g. SSL verification (certificate validity, proper redirect, etc.), subdomain takeover check or SQL injection check.
To do that, clone https://github.com/CERT-Polska/Artemis-modules-extra/ inside the Artemis directory and use:
docker compose -f docker-compose.yaml -f Artemis-modules-extra/docker-compose.yml up --build
If you want to start multiple instances of a module to speed up scanning, use a command such as:
docker compose -f docker-compose.yaml -f Artemis-modules-extra/docker-compose.yml up --build \
--scale=karton-nuclei=10 \
--scale=karton-bruter=10 \
--scale=karton-port_scanner=10
For the full list of available configuration options you may set in the .env file, see Configuration options.
Note
If you get an error that docker compose is not a valid command, that means that Docker Compose
plugin is not installed. Please follow the instructions from https://docs.docker.com/compose/install/linux/#install-using-the-repository
The old docker-compose syntax is not recommended.
Adding targets to scan
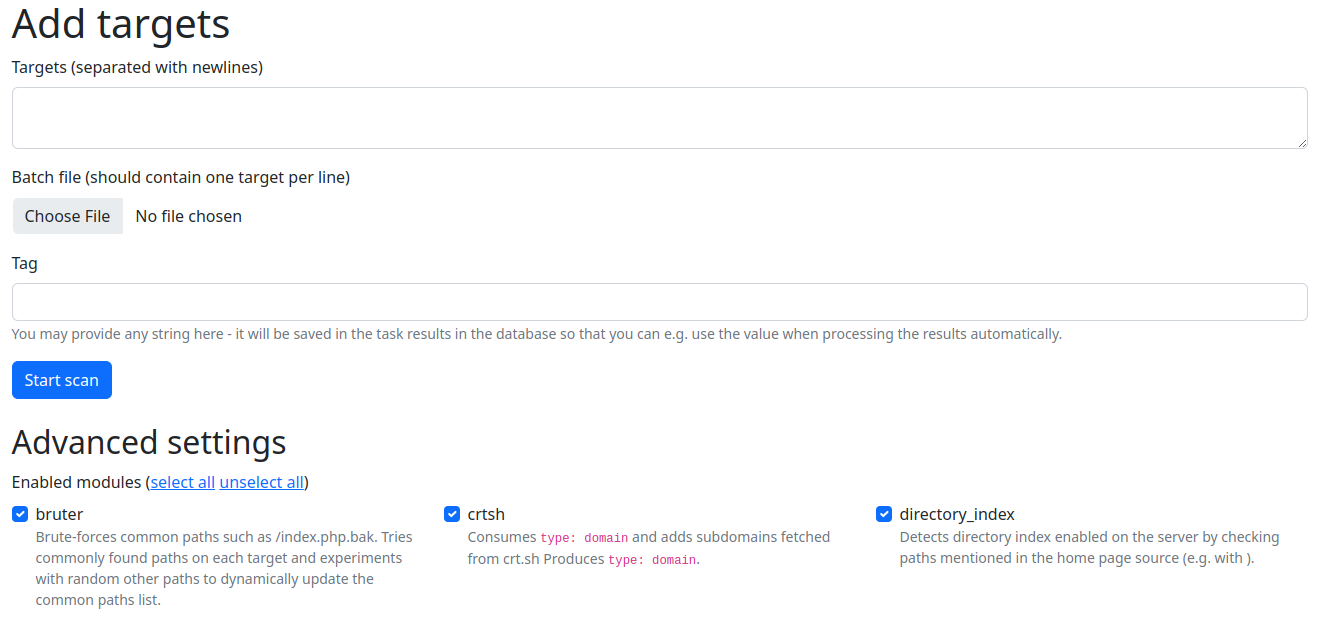
To add targets to be scanned, select Add targets from the top navigation bar. Artemis takes input
in the form of entries separated with newlines. Artemis works with both IPs and domains. It also supports
IP ranges, both in the form of 127.0.0.1-127.0.0.10 or 127.0.0.0/30 and host:port syntax - in the latter
case, no port scanning will be performed.
If a URL is provided, the host from this URL will be scanned.
To be later able to filter various types of targets, provide a tag in the Tag field. You may also choose what modules will be executed, to increase scanning speed if you need only to check for a subset of vulnerabilities.
Viewing results
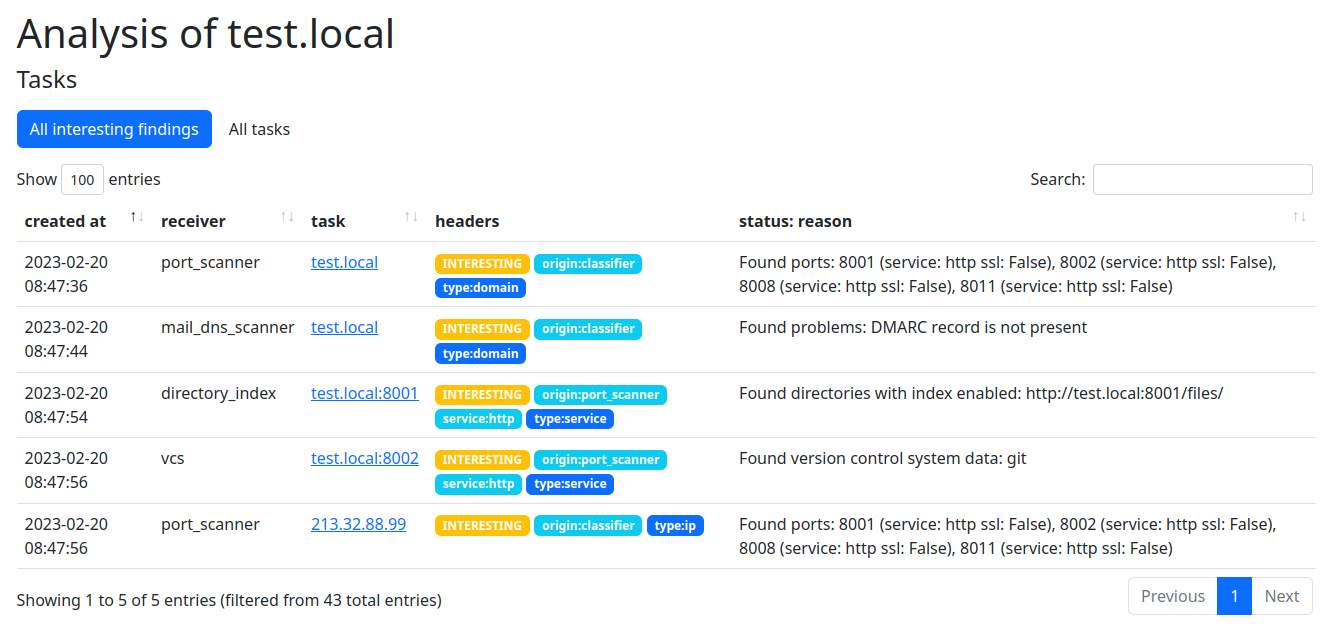
To view results, click the View results link in the top navigation bar:
Exporting reports
Besides viewing the raw results, you may want to generate HTML reports containing descriptions of found vulnerabilities, so thay you can notify the administrators to get the vulnerabilities fixed.
To do that, please refer to Generating reports to be sent.